Archived web site for RVAsec 2015 can be viewed here
All of the RVAsec 2015 conference videos are online and available for viewing at RVAsec’s YouTube channel.
Archived web site for RVAsec 2015 can be viewed here
All of the RVAsec 2015 conference videos are online and available for viewing at RVAsec’s YouTube channel.
We have finally recovered from RV4sec and wanted to bring you a quick recap! We sold 386 tickets this year, and was on par for attendance from the previous year. It was great to see so many new faces this year and we hoped everyone had a great time.
What were thrilled to bring you:

What to expect in the coming weeks:
Thanks again to all our our speakers, sponsors and volunteers!
Next year, RVAs5c will be June 2-3, 2016.
See you next year.
Jake and Chris
Did you know you can transfer an RVAsec ticket to a co-worker or friend directly in Eventbrite?
Log in to your account and go to My Tickets (you may need to create an account using the email address you registered).
Then you can view your Current Orders (select RVAsec), and “Edit details” for the ticket. Changing the “Contact Information” will update the name of the person registered to check in at the conference. You can also change the questions asked at registration, which will help us plan for parking, catering and other items.
Also, please note that no refunds for training or the conference will be issued after May 26th.
Paul Bruggeman from HackRVA provided us with an update on the badges!
Badge Design

The printed circuit board, or PCB, is the backbone of any circuit board. It supplies the physical strength and fundamental wiring for the board. It also determines the minimum size.
The circuit design artwork is  drawn, usually with special software but hobbyists sometimes just draw them by hand. The gEDA software suite has a component called “pcb” that was used to draw the badge.
drawn, usually with special software but hobbyists sometimes just draw them by hand. The gEDA software suite has a component called “pcb” that was used to draw the badge.
Badge Etching

The PCB board is fiberglass-reinforced epoxy laminated with a thin copper sheet which is etched away using ferric chloride to recreate the artwork.
One goal of this year’s badge was to use a professional process to cover the  boards with the acid resist. Attempts last year worked but were not consistent.
boards with the acid resist. Attempts last year worked but were not consistent.
Badge Cutting

Once the boards are etched they have to be cut down to final size. PCBs are tough material to cut.
The addition of a sheet metal cutter this year has made it much easier to do. The steel blade is 1/2″ thick and the whole thing weighs 60 lbs!
The steel blade is 1/2″ thick and the whole thing weighs 60 lbs!
Badge Parts

With the boards cut down, the next process is to put the surface mount parts on. Most of the 50+ parts are surface mount. This means they have no wires to solder, because they have metals pads that melt and attach when heated to 510F degrees.
The process of installing the parts is called “pick and place.” Not very  complicated, but it can be tedious to do, especially 350 times!
complicated, but it can be tedious to do, especially 350 times!
Badge pick+place
 First a solder paste containing thousands of beads of tin is drawn across a stencil that leaves the sticky grey paste where the parts will be placed. This stencil is etched copper foil. Stencils can also be plastic or steel.
First a solder paste containing thousands of beads of tin is drawn across a stencil that leaves the sticky grey paste where the parts will be placed. This stencil is etched copper foil. Stencils can also be plastic or steel.
The board then makes its way down the volunteer assembly line where parts 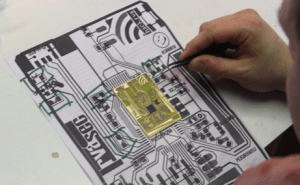 are carefully placed on the solder paste. We have had the help of over a dozen HackRVA people so far this year.
are carefully placed on the solder paste. We have had the help of over a dozen HackRVA people so far this year.
Badge Cooking
 The solder paste has to be melted or “re-flowed” to electrically connect the parts to the PCB. This currently is not very hi-tech: $20 donated ovens. A volunteer last year built a micro- controlled unit but the heating element died on it.
The solder paste has to be melted or “re-flowed” to electrically connect the parts to the PCB. This currently is not very hi-tech: $20 donated ovens. A volunteer last year built a micro- controlled unit but the heating element died on it.
The manual ovens require attention. Failures are usually of the distracted  human type. We had a board last year survive a 5-hour session underneath the oven, and it worked fine–though it looked like burnt toast!
human type. We had a board last year survive a 5-hour session underneath the oven, and it worked fine–though it looked like burnt toast!
Badge Wrap-up

The last things to go on are the hand- soldered parts: infrared transmitter and receiver, piezo buzzer, USB connector, USB detection wire, and the LCD panel.
If you plan on doing any software development we recommend the reset  button option (red in picture) which can be soldered across the middle and far right pin on the lower center 5-pin programming header.
button option (red in picture) which can be soldered across the middle and far right pin on the lower center 5-pin programming header.
Design: Paul, Morgan
Electronics: Paul
Coordinator: Morgan
Etch: Paul, Jon, Aaron
Pick+place: Jon, John, Bill, John, Yijie, Sidney,
Thad, Tony (so far)
Tickets for RV4sec 2015 are now on sale!
Early registration price is only $125 for great speakers, food and beverages, t-shirt, swag, parking and more!
RV4sec’s base ticket price for 2015 is $150 and will be in place on 3/14–so don’t wait! And if that’s not enough incentive to purchase your tickets early, late registrations (after 5/17) will be $225!
Don’t forget all the things you get with registration, including 2 full days of talks, meals, parking, snacks, drinks, reception, after party, prizes, a capture the flag contest, t-shirt & swag!
So, to recap the conference prices:
If you are unable to attend due to the price, please contact us to discuss as we do have stipends available and volunteer opportunities are a great way to get in for free! Once again there will be no tickets sold at the door, and don’t forget that RV4sec has sold out every year–so don’t wait!
The call for papers for RVAsec 4 is now open!
Conference: June 4-5th, 2015
Location: Richmond, VA
CFP Submission Deadline: March 14th, 2015 at 11:59 PM Eastern
RVAsec is a Richmond, VA based security convention that brings top industry speakers to the midatlantic region. In its third year, RVAsec 2014 attracted 350 security professionals from across the country. For 2015, the conference is a two day and dual-track format, with a mixed focus on technical and management/business presentations.
All talks must be 55 minutes in length, and submissions will need to select either technical or business/management tracks.
Join us and enjoy the perks!
For more information and requirements, or to submit, please visit:
If you are interested in running a training class on June 3rd, please email us at info@rvasec.com with the following information:
1) Title Of Class
2) Overview of Class (enough details that we can properly understand what students will learn!)
3) Instructor Name
4) Instructor Bio
5) Desired Class Size
6) Student Prerequisites:
7) Proposed Cost / Amount Required Per Student:
CFP deadline is Friday, March 14th, 2015 at 11:59 PM Eastern!
RVAsec 4
June 4-5th, 2015
Richmond, VA, on the Virginia Commonwealth University campus
RVAsec is a Richmond, VA based security convention that brings top industry speakers to the midatlantic region. In its third year, RVAsec 2014 attracted 350 security professionals from across the country. For 2015, the conference is a two day and dual-track format, with a mixed focus on technical and management/business presentations.
All talks must be 55 minutes in length, and submissions will need to select from one of two tracks:
The following types of presentations will not be accepted:
RVAsec will hold no copyright on presentation content, but all speakers will be required to provide approval to post slides and video recordings of the talk on the RVAsec or other web sites.
Speaker Perks
RVAsec has a limited travel budget, but speakers who request travel
assistance may be eligible for:
If you are interested in running a training class on June 3rd, please email us at info@rvasec.com with the following information:
1) Title Of Class
2) Overview of Class (enough details that we can properly understand what students will learn!)
3) Instructor Name
4) Instructor Bio
5) Desired Class Size
6) Student Prerequisites:
7) Proposed Cost / Amount Required Per Student:
 Dwayne McDaniel
Dwayne McDanielEver wish you could set traps for intruders in your environment? While you can’t rig explosions or rolling boulders when someone attacks your servers, you can set up false credentials that trigger alarms you can act against. That is the whole idea behind honeytokens!
Come to this session to learn how honeytokens work
About Dwayne – Dwayne has been working as a Developer Relations professional since 2015 and has been involved in tech communities since 2005. He loves sharing his knowledge, and he has done so by giving talks at over a hundred events worldwide. Dwayne currently lives in Chicago. Outside of tech, he loves karaoke, live music, and performing improv.
 Andrea Matwyshyn
Andrea MatwyshynWhen the 2023 National Cybersecurity Strategy called for “shifting liability to promote secure development practices,” the response from the security (and legal) community often overstated the novelty of the proposal. We have already been living with (various forms of) software liability for confidentiality, integrity, and availability failures for over two decades. This talk clarifies the legal landscape of both what already exists and the likely paths for the future. Cautioning against various security dystopias including Hannah Arendt’s “cybernation,” this talk offers suggestions on buildouts to existing threat modeling frameworks to explicitly consider factors used by courts and regulators to determine liability. These buildouts can better align the security team and in-house counsel in a joint defensive enterprise. But, two scaling issues will remain: the need for a technology regulator of last resort (a “TRoLR”) and a security community-driven model of professionalism.
About Andrea – Dr. Andrea Matwyshyn is a full professor in the law school and engineering school at Penn State, the Associate Dean of Innovation at Penn State Law, and the founding faculty director of both the Penn State PILOT Lab (Policy Innovation Lab of Tomorrow), an interdisciplinary technology policy lab, and the Manglona Lab for Gender and Economic Equity, a technology equity lab and clinic.
She has also worked in both the private and public sector, most recently in 2023 as a Senior Special Advisor on Information Security and Data Privacy to the U.S. Consumer Financial Protection Bureau’s Office of Enforcement and a Senior Special Advisor on Law, Technology, and the Digital Economy to the U.S. Federal Trade Commission’s Bureau of Consumer Protection. Her first hackercon talk was at BlackHat USA in 2003, and she has previously served as a specialty reviewer on the DEF CON CFP Review team.
Dwayne has been working as a Developer Relations professional since 2015 and has been involved in tech communities since 2005. He loves sharing his knowledge, and he has done so by giving talks at over a hundred events worldwide. Dwayne currently lives in Chicago. Outside of tech, he loves karaoke, live music, and performing improv.
Twitter: @mcdwayne
Who Goes There? Actively Detecting Intruders With Cyber Deception Tools
Ever wish you could set traps for intruders in your environment? While you can’t rig explosions or rolling boulders when someone attacks your servers, you can set up false credentials that trigger alarms you can act against. That is the whole idea behind honeytokens!
Come to this session to learn how honeytokens work

RVAsec is pleased to announce Rapid7 as a Silver level sponsor for RVAsec 11!

Rapid7 is engineering better security with simple, innovative solutions for IT security’s most critical challenges. Our security data and analytics solutions collect, contextualize, correlate, and analyze the security data you need to dramatically reduce threat exposure and detect compromise in real-time.
Copyright © 2024, RVAsec. Proudly powered by WordPress. Blackoot design by Iceable Themes.
